It’s a rare thing these days – without a thousand notifications or an online meeting – to have a plan come together. And yet, that’s what happened over the last few weeks as I started to think about this post. As if on cue, to remind me that I’d decided to write about phishing, email started to flood my Inbox.
Every day or couple of days for over a month now, I’ve received a flurry of requests to sign invoices, allegedly from DocuSign.
 I’ve also received notices from what I’ll call the “other” PayPal that my account has been limited due to suspicious activity or because I’ve violated the terms of an agreement.
I’ve also received notices from what I’ll call the “other” PayPal that my account has been limited due to suspicious activity or because I’ve violated the terms of an agreement.
I’ve even been notified that “Walgreens” had a special gift for me worth at least $100. I’d just need to fill out a survey, select my gift from “several exclusive offer rewards” – worth atleast (sic) $100 – and I’d be guaranteed to be a victim.
Some emails, like the “Walgreens” one, are so obviously phishy that it’s easy to tell the pain from clicking on the link to “Get Started Here!” will be felt long after the original message has been deleted. The logo was close, but the rest of the message didn’t look at all like a message from Walgreens. Multiple fonts. Multiple shades of red. Unsubscribe was spelled incorrectly…twice. And, as if those signs weren’t enough to tip me off that there wasn’t an exclusive reward on the other side of a click of the mouse, the sender’s address wasn’t even remotely close to something related to walgreens[.]com. Instead, the address referenced a domain name that was recently registered.
Some phishing emails are more of a mixed bag, especially at first glance.
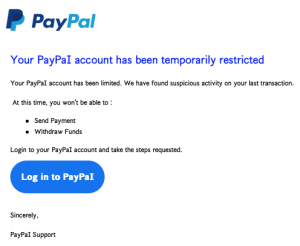
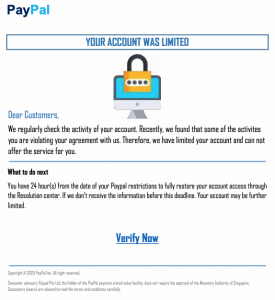
One of the fake PayPal emails had the right logo, but suggested I needed to log into PayPaI with a capital “I” rather than a lower case “l”. The other phishing attempt displayed a rather ominous image of a computer with a lock over it and a rather plain version of PayPal’s logo. Both contained reference numbers in the subject line and the senders’ addresses were a combination of letters and numbers that looked like they were created by a random password generator.
But not all phishing emails are so…blatantly…obviously…attempts to get us to share our credentials. They look like the real thing or are copies that are “good enough” to trick unsuspecting users with only a second or two to make a judgment call into believing they are real.
They look like legitimate requests that need our attention. The fake DocuSign emails, for example, included links to the legitimate website for DocuSign and for account login. The messages didn’t contain any telltale spelling errors.
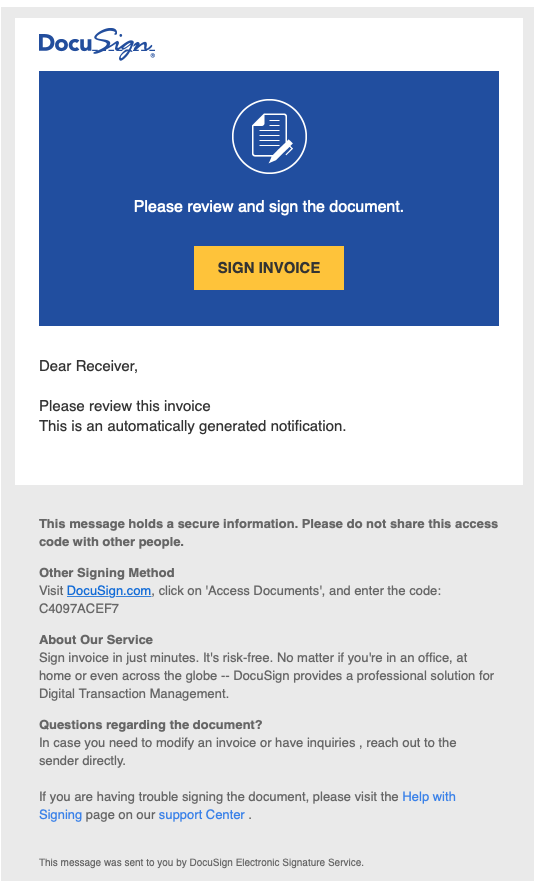
Those same messages also implored me with urgent calls to action via the subject lines:
You received notification from DocuSign Electronic Service • You received invoice from DocuSign Electronic Signature Service • You got invoice from DocuSign Signature Service
And they provided me with convenient buttons to perform a variety of actions:
Sign Invoice • See Invoice • Review Invoice • See Document
BUT…
They were still phishing emails. Just like the phishing emails referenced in an alert last fall, these email messages contained links to Google docs.
It’s hard to believe that 25 years after the first recorded mention of phishing, we’re still dealing with the issue. But then again, phishing works…enough of the time to make it worthwhile.
The original post on analyzing email headers will have to wait. Time to go clean my inbox and empty my trash.
Need to report a fraudulent email that claims it’s from Walgreens, PayPal or DocuSign?
For Walgreens, click here. For PayPal, click here. For DocuSign, click here.

