I wasn’t planning to write a blog post this week, but sometimes something happens, and the creative juices start flowing. Or an opportunity is presented, and you just can’t help yourself.
Yesterday I received an email from a vendor trying to sell me cybersecurity services, or rather to get me to become a partner and resell the vendor’s services. The subject line of the email was meant to be an attention grabber. It read:
Customer Cybersecurity and Application Performance Issues? You want to read this email!

Okay, I thought, I’ll bite. One mouse click and the email was open.
Wait…whaaat? Is this a joke?
I sat at my desk stunned for a second or two and then burst out laughing. My email address was one of 180 plus which had the words secure, cyber, tech, data, and more in their domain names.
Then, I read the first sentence in the message.
Are you trying to solve a wide array of technology challenges for your customers, from application performance to cybersecurity threats?
No way!
Have you ever laughed so hard that you’ve had to consciously stop yourself from laughing because you know if someone is surreptitiously recording you from afar with their smartphone that you will become a new meme for the acronym that begins ROTF?
But wait…there’s more. The message from the vendor contained a link so I could complete an Authorized Reseller Agreement.
Clearly, someone made a mistake, a very big mistake. In a second email, sent about three hours after the first, someone from the vendor apologized for the marketing team’s mishandling of the communication and assured those on the recipient list that it wouldn’t happen again.

At that point, however, the damage was done…. the cat was out of the bag…there was no closing the barn door to keep the horse inside. One of the 180 plus recipients asked if anyone had any experience with the vendor that sent the email. Some of the recipients sent messages asking to be removed from the list. Others took a more humorous approach to the gaffe that had made us a community and at least one recipient started a new thread. Over 12 hours after the original email was sent, replies were still streaming into my inbox until the last one on the original thread arrived. It simply said “STOP!!!”
Seriously, though…this is how, as one of the recipients reminded me, servers crashed in the early days of email. It’s also why every person in a company should understand what cybersecurity is and why it’s important.

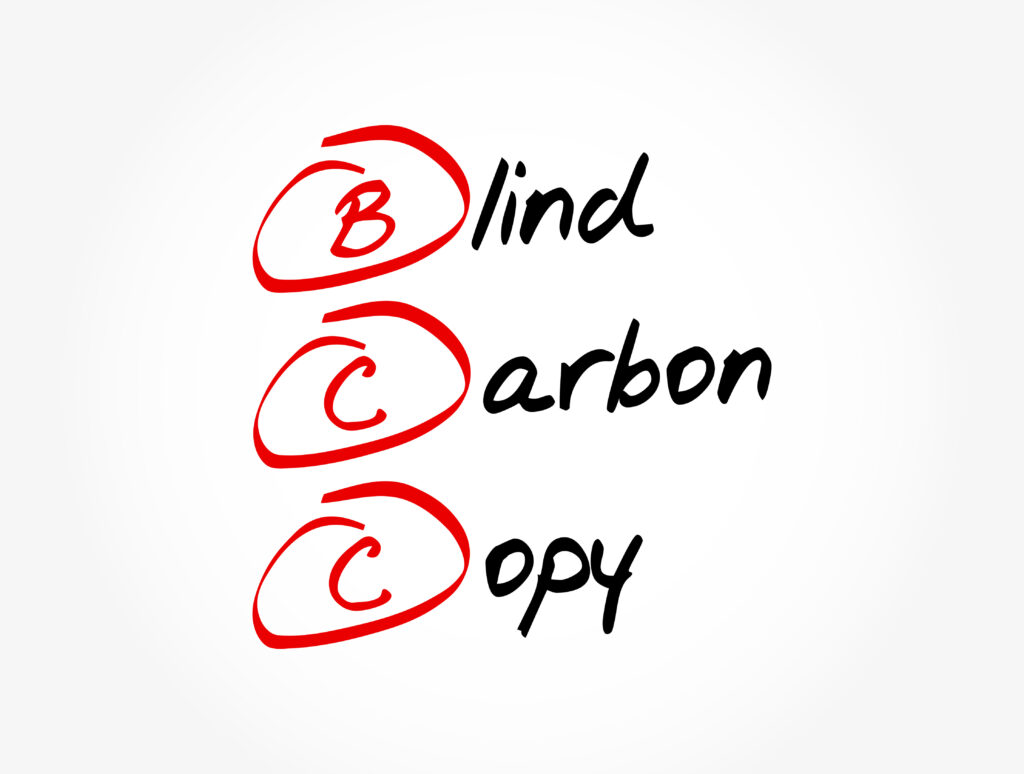
This one simple oversight – we’ll call it that – illustrates perfectly how easy it is to compromise the C in C-I-A (Confidentiality, Integrity, Availability). Unauthorized sharing – whether it’s accidental because someone forgets to use BCC (blind carbon copy) or intentional – is still unauthorized sharing. It also illustrates why risk management needs to be part of a company’s cybersecurity strategy, and why policies and procedures that address email security, business continuity, and disaster recovery are critical.
In this case, the compromise was a list of prospects. What if the information that was disclosed in the email was something else? What if the mistake had gone unnoticed and no apology email was sent? What if someone on the list of prospects decided to sell it? What if…
That’s why as funny as it was, this type of oversight, mistake, or error – call it what you like – is really no laughing matter. I doubt anyone who received the email is likely to want to do business with this vendor in the immediate future. And, since news travels fast, there will be others who choose to exercise the same due diligence.
I’m pretty confident that the same thing won’t happen again…at least in the near future…in the marketing department at this company. Besides serving as a glaring reminder of why unsend became a feature, the takeaway from this cautionary tale is that it could happen in any marketing department at any company, or to anyone for that matter, who doesn’t take the time to proofread an email before hitting send.